The Solution:
- Align with CyberArks’s main target audience type – people who work in the information technology sector – we went for a bespoke and bold graphic-novel book style featuring two intertwined worlds; the office environment and the world of data.
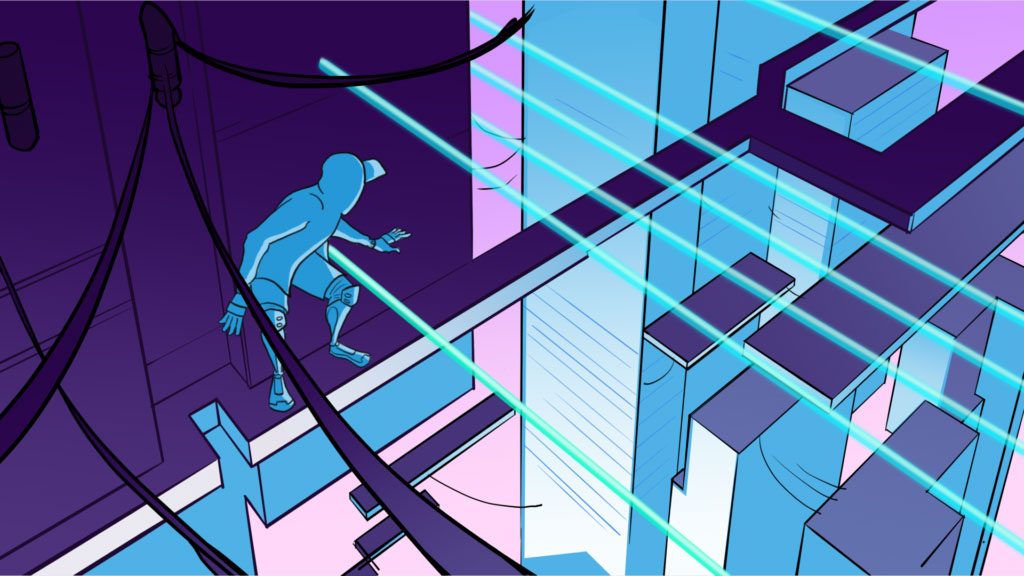
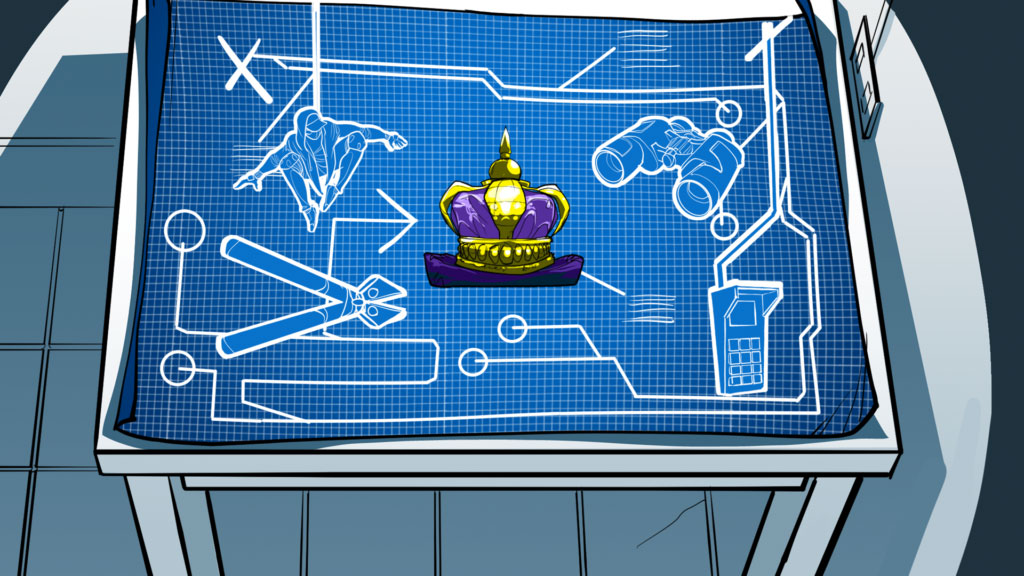
- A ninja like hacker tries to intrude the system to steal the ‘Crown Jewels’. The Crown Jewels are a companies most critical assets – client data, intellectual property, service up time etc.
- Modular content – from the start we set up to make the assets as versatile and modular as possible – e.g. the animation could be edited down to short sections and be used with overlaid text for bitesize social media clips, for use on LinkedIn, Facebook, X, and Instagram.
- Gamification – we also created a scenario-based ‘choose your own adventure style’ interactive PDF, in which the player needs to think like a hacker in order to complete the game and score points. The illustration style is the same as in the animation.
What we did:
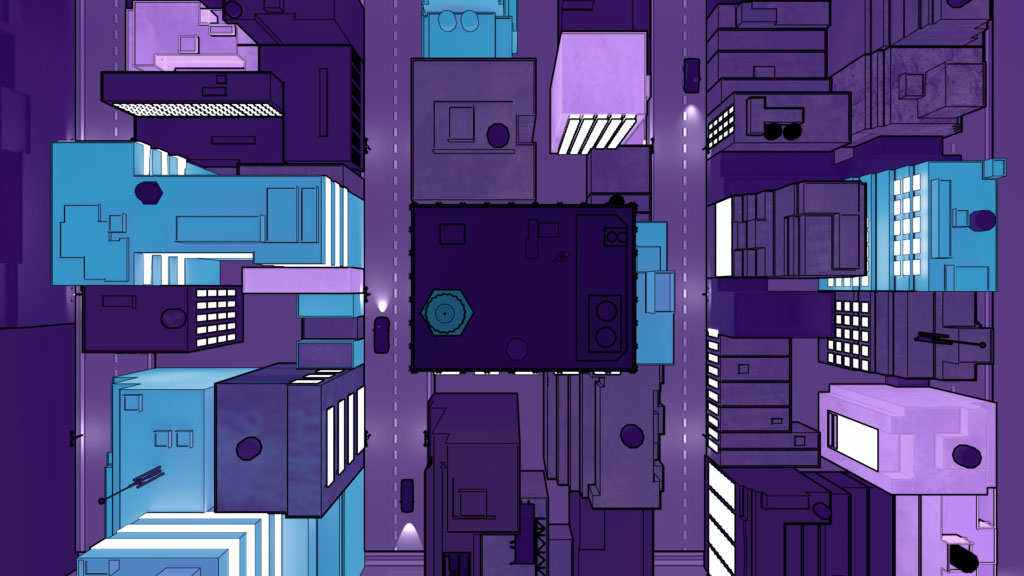
Typically the subject matter is marketed in a very dry and bland way. We were asked to create something engaging and vibrant, a creative approach that would stand out from the crowd, and competitors. With careful consideration we agreed that a comic book style, graphic novel illustration style would work best and we developed a dramatic story and visuals around two intertwined worlds; the office environment, and the data world.
“This is your Crown Jewels, your most critical assets (client data, intellectual property, service up time etc). Like anything precious, it always needs protection from unscrupulous characters. But unlike the physical world, it’s more a question of when, than if, an attacker will get inside. Whoever they are, they know privilege account credentials are the route to those crown jewels.”
The story
The challenge was to inform the viewer about privileged access security in an engaging and captivating way, while avoiding overloading them with technical jargon. With that in mind how do you show a world in which all activity circles around ‘invisible’ data?
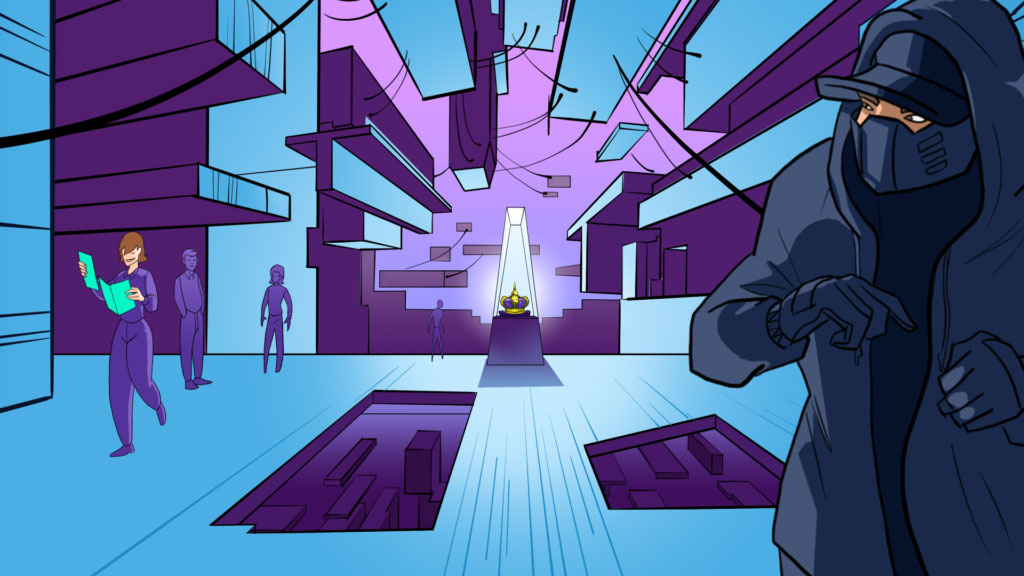
Taking off in an office environment we are quickly pulled into a world behind the screen, with streaming data and the crown jewels at its centre. System intruders and unscrupulous characters are hiding inconspicuously, advancing steadily and waiting for their chance to finally strike and steal the crown jewels.
The catastrophe is perfect, but could have been avoided if there had been Cyberark’s multi-layered privileged access security protection in place!
Our process
If you are unfamiliar with the animation production process, this blog post What to expect when you work on an animation with Sliced Bread might serve to help you, it provides a complete guide on how we typically approach our projects, from concept to final delivery. It also provides information on how we structure our fees and plan the production schedule.
Contact us
Would you like to know more about how animation and technology can support your digital marketing requirements? Please feel free to drop us a line at info@sbanimation.com, or give us a call on +44 (0)207 148 0526. We would be happy to help.
We also post industry related content to our LinkedIn company page, why not give us a follow?